Overview
This Cyber Heads-up has been updated to include a PowerShell command to determine whether an Exchange server has already been compromised.
Assura’s Defensive Security Operations Center (SOC) is monitoring recently reported zero-day vulnerabilities in Microsoft Exchange 2013, 2016, and 2019 being exploited in the wild.
“The first vulnerability, identified as CVE-2022-41040, is a Server-Side Request Forgery (SSRF) vulnerability, while the second, identified as CVE-2022-41082, allows remote code execution (RCE) when PowerShell is accessible to the attacker,” Microsoft said.
In their MSRC blog, Microsoft stated: “At this time, Microsoft is aware of limited targeted attacks using the two vulnerabilities to get into users’ systems.”
The company added that the CVE-2022-41040 flaw can only be exploited by authenticated attackers. Successful exploitation then allows them to trigger the CVE-2022-41082 RCE vulnerability.
Microsoft says Exchange Online customers do not need to take any action because the company has detections and mitigations in place to protect customers.
“Microsoft is also monitoring these already deployed detections for malicious activity and will take necessary response actions to protect customers. […] We are working on an accelerated timeline to release a fix,” Microsoft added.
According to Vietnamese cybersecurity outfit GTSC, who first reported the ongoing attacks, the zero-days are chained for the purpose of deploying China Chopper web shells to:
- Achieve persistence
- Commit data theft
- Move laterally through victim networks
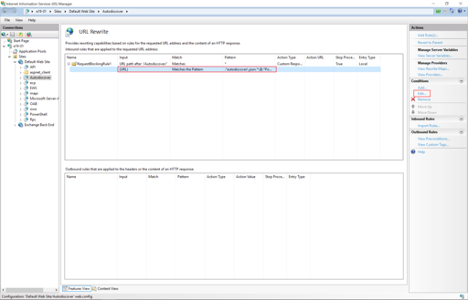
Microsoft has confirmed that the following URL Rewrite Instructions, which are currently being discussed publicly, are successful in breaking current attack chains.
Here are the mitigation steps:
1. Open IIS Manager.
2. Expand Default Web Site.
3. Select Autodiscover.
4. In the Feature View, click URL Rewrite.
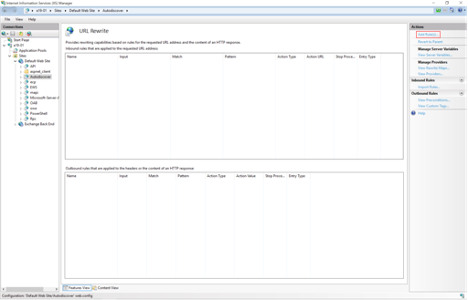
5. In the Actions pane on the right-hand side, click Add Rules.
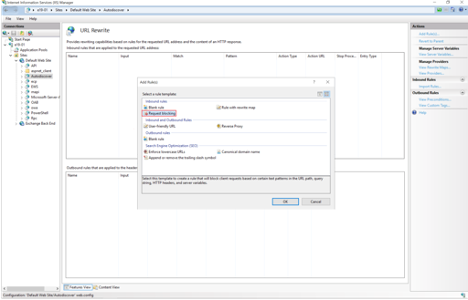
6. Select Request Blocking and click OK.
7. Add the string .*autodiscover\.json.*\@.*Powershell.* and click OK.
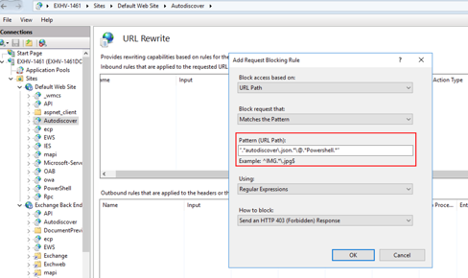
8. Expand the rule and select the rule with the pattern .*autodiscover\.json.*\@.*Powershell.* and click Edit under Conditions.
9. Change the condition input from {URL} to {REQUEST_URI}
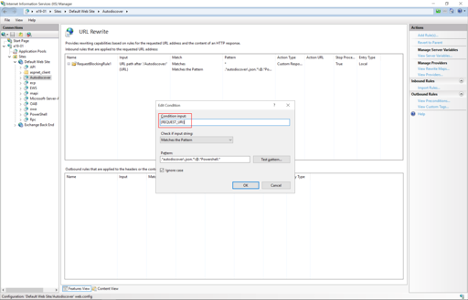
10. Click OK.
Impact: There is no known impact to Exchange functionality if the URL Rewrite module is installed as recommended.
Authenticated attackers who can access PowerShell Remoting on vulnerable Exchange systems will be able to trigger RCE using CVE-2022-41082. Blocking the ports used for Remote PowerShell can limit these attacks. They are:
- HTTP: 5985
- HTTPS: 5986
To determine whether an Exchange server is already compromised, run the following PowerShell command to scan IIS logs for indicators of compromise:
Get-ChildItem -Recurse -Path -Filter ".log" | Select-String -Pattern 'powershell.autodiscover.json.\@.200'
Assura’s Take
We strongly recommend that organizations with on-premises Exchange implement this mitigation IMMEDIATELY.
Aside from taking the above mitigation steps, Assura recommends putting webshell detection in place on your on-premises Exchange servers. A tool such as Huntress, which Assura uses for events such as this is an excellent example of the Advanced Persistent Threat (APT) detection needed to address these types Zero-Day vulnerabilities.
References:
