Overview of Follina
On Friday, May 27th, 2022, @nao_sec announced on Twitter that they had discovered a novel attack technique utilized in a malicious document (maldoc) submitted from a Belarus IP address to VirusTotal. The new technique uses Microsoft’s Microsoft Support Diagnostic Tool (MSDT) to retrieve and execute malicious code from a remote URL. Microsoft is currently working on long-term mitigations and has released short-term workarounds and detection rules to help prevent and detect exploits of this attack in the wild. This zero-day vulnerability has been dubbed, “Follina” and has been assigned the CVE number CVE-2022-30190.
What We Know About the Follina Zero-day Exploit Attack
Microsoft’s Office suite, and presumably any other Microsoft product using MSDT for troubleshooting (Xbox Live, GameBar, the Windows Store, etc.), are affected by this zero-day exploit with no patch available at the time this Cyber Heads-up written. This zero-day vulnerability allows for remote code execution, which means that malicious code is run, with a single click and potentially zero clicks. The only requirement to run the malicious code is to open the maldoc in a Microsoft Office application. Some security researchers have demonstrated execution of the malicious code merely by previewing the document in Windows File Explorer or Outlook.
“Under the hood”, Microsoft Office documents are Zip archives that contain a number of different components (e.g., graphics files, text content, formatting information, and Visual Basic macro code. What is being exploited in this zero-day is the word/_rels/document.xml.rels file.
Within the document.xml.rels file an attacker can place a URL to retrieve remote HTML.
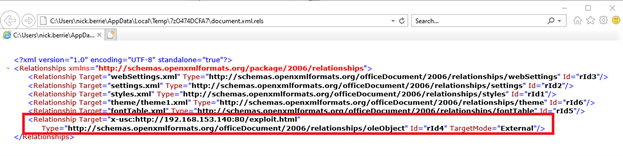
The attacker hosts a malicious HTML file to load code and execute commands on the system that the malicious file downloads using the ms-msdt MSProtocol URI scheme. These commands can be used to load and execute the malware on the system to obtain remote access or retrieve sensitive information from the victim’s device. Here, Assura’s Director of Offensive Security Operations, Nick Berrie, uses publicly available a Proof-of-Concept (POC) python script developed by Cas van Cooten (@chvancooten) to demonstrate this exploit.
Assura’s Take on the Follina Zero-day Exploit
The security community is currently evaluating effective responses to this zero-day vulnerability. Currently, Assura recommends that all organizations warn their users to exercise extreme caution over-and-above that already recommended before opening Microsoft Office documents, especially those they did not expect to receive.
Microsoft has released the following guidance as a workaround until long-term mitigation can be created:
Disable the MSDT URL Protocol
Disabling the MSDT URL protocol prevents troubleshooters from being launched as links including links throughout the operating system. Troubleshooters can still be accessed using the Get Help application and in system settings as other or additional troubleshooters.
Follow these steps to disable the MSDT URL protocol:
- Run Command Prompt as Administrator.
- Back up the registry key by executing the command “
reg export HKEY_CLASSES_ROOT\ms-msdt filename“. - Execute the command “
reg delete HKEY_CLASSES_ROOT\ms-msdt /f”.
To undo the workaround:
- Run Command Prompt as Administrator.
- Restore the previous registry key, by executing the command “
reg import filename”
This registry key can be deployed via Group Policy Object in Windows Active Directory or via PowerShell script using Microsoft System Center Configuration Manager (SCCM). You can also use Mobile Device Management solutions such as Microsoft Endpoint Manager.
Microsoft Defender Detections & Protections Against Follina Zero-day Exploit
Customers with Microsoft Defender Antivirus should turn on cloud-delivered protection and automatic sample submission. These capabilities use artificial intelligence and machine learning to quickly identify and stop new and unknown threats.
Customers of Microsoft Defender for Endpoint can enable the attack surface reduction rule “BlockOfficeCreateProcessRule” that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy. For more information see the Attack surface reduction rules overview.
Microsoft Defender Antivirus provides detections and protections for possible vulnerability exploitation under the following signatures using detection build 1.367.719.0 or newer:
- Trojan:Win32/Mesdetty.A
- Trojan:Win32/Mesdetty.B
- Behavior:Win32/MesdettyLaunch.A
- Behavior:Win32/MesdettyLaunch.B
- Behavior:Win32/MesdettyLaunch.C
Microsoft Defender for Endpoint provides customers with detections and alerts. The following alert title in the Microsoft 365 Defender portal can indicate threat activity on your network:
- Suspicious behavior by an Office application
- Suspicious behavior by Msdt.exe
Additionally, if the calling application is a Microsoft Office application, by default, Microsoft Office opens documents from the internet in Protected View or Application Guard for Office, both of which prevent the current attack.
Assura has confirmed through direct testing that Microsoft ATP for Outlook Email Attachments and Defender for Office 365 is successfully catching Proofs-of-Concept, which indicates Microsoft is working on detections in addition to the long-term mitigations.
Assura’s SOC is monitoring for known signatures of this exploit via our Managed SIEM service.
If you’re an Assura client, please do not hesitate to reach out to your Virtual ISO or Assura SOC Concierge if you have questions about this technique or how you can better defend against it. Otherwise, please contact us at [email protected].
References
@Nao_sec Tweet – https://twitter.com/nao_sec/status/1530196847679401984
Microsoft CVE-2022-30190 Guidance – https://msrc-blog.microsoft.com/2022/05/30/guidance-for-cve-2022-30190-microsoft-support-diagnostic-tool-vulnerability/
Kevin Beaumont – Follina Write-up – https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e
Huntress Labs – Follina Write-up – https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug
