Overview
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an urgent advisory concerning the exploitation of Unitronics programmable logic controllers (PLCs) within the Water and Wastewater Systems (WWS) Sector. These critical systems manage various aspects of water treatment and distribution, and cyber threat actors have targeted these PLCs, posing a significant risk to the integrity of water facilities. An identified incident involving a Unitronics PLC at a U.S. water facility resulted in immediate offline operations, thus ensuring no risk to the water supply. However, this attack highlights the vulnerability of these systems and the urgency for comprehensive cybersecurity measures.
Technical Analysis
The attackers likely accessed the affected Unitronics Vision Series PLC with the management console through cybersecurity weaknesses, notably exploiting default password settings (“1111”) and exposure to the internet. These vulnerabilities enabled unauthorized access, potentially jeopardizing critical functions such as pump control, chemical dosing, compliance data gathering, and alarm systems.
Assura’s Take
Securing critical infrastructure, especially within the Water and Wastewater Systems Sector, demands immediate action and robust cybersecurity measures. By addressing vulnerabilities through password management, access controls, network segmentation, and regular updates, organizations can fortify their defenses against cyber threats. Implementing proactive measures, including documenting and adhering to an information security program, conducting vulnerability assessments and penetration testing, and implementing security monitoring is pivotal in safeguarding these vital systems and ensuring uninterrupted, safe water supply and wastewater management for communities.
Assura recommends that organizations take the following actions to help mitigate risks related to this vulnerability:
- Change the Unitronics PLC default password—validate that the default password “1111” is not in use.
- Require multifactor authentication for all remote access to the Operational Technology (OT) network, including from the IT network and external networks.
- Disconnect the PLC from the internet. If remote access is necessary, implement a Firewall/VPN in front of the PLC to control network access to the remote PLC. A VPN or gateway device can enable multifactor authentication for remote access even if the PLC does not support multifactor authentication.
- Back up the logic and configurations on any Unitronics PLCs to enable fast recovery. Become familiar with the process for factory resetting and deploying configurations to a device in the event of being hit by ransomware.
- If possible, utilize a TCP port that is different than the default port TCP 20256. Cyber actors are actively targeting TCP 20256 after identifying it through network probing as a port associated to Unitronics PLC. Once identified, they leverage scripts specific to PCOM/TCP to query and validate the system, allowing for further probing and connection. If available, use PCOM/TCP filters to parse out the packets.
- Update PLC/HMI to the latest version provided by Unitronics.
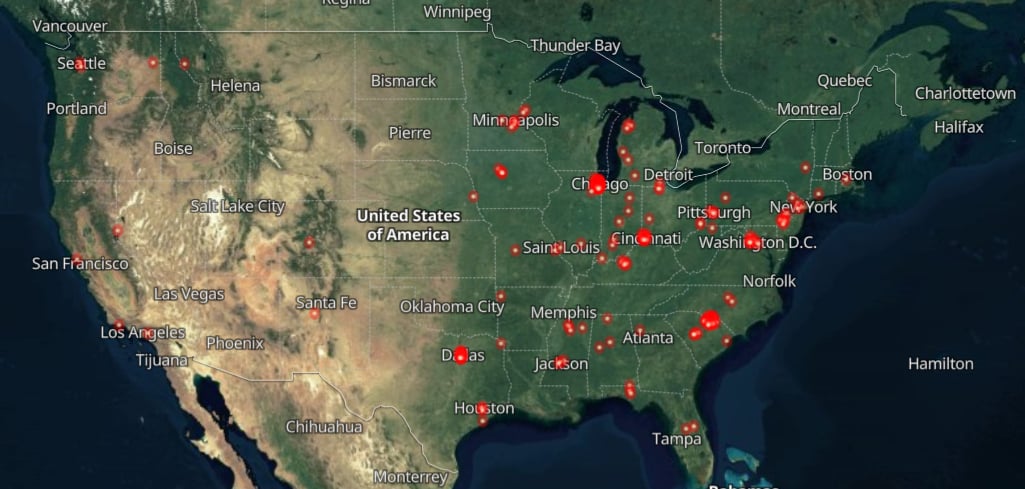
At the time of this writing, Assura has identified over 200 PLCs potentially affected by this issue exposed to the Internet in the U.S. and over 1,800 world-wide.
References:
