Overview
Assura’s Offensive Security Operations Team has been looking into MDSec’s Dominic Chell’s research into the recent Microsoft Office Outlook updates where Dominic found that there is a privilege escalation vulnerability within Outlook.
Via this vulnerability, a remote attacker can create a malicious Outlook Appointment Reminder which when triggered, will authenticate the victim to a remote SMB share via a UNC path to obtain the victim’s NTLM password hash.
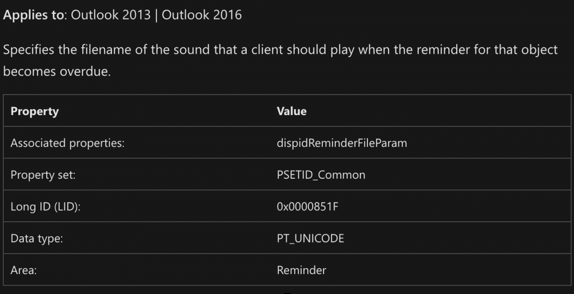
Within Outlook, users can create Appointments that have a reminder flag set on them upon sending. If you’ve ever received a reminder prompt from Outlook you are likely familiar with the “ding” sound that it plays. Well, Dominic discovered by analyzing the Microsoft audit script for CVE-2023-23397 (https://github.com/microsoft/CSS-Exchange/blob/a4c096e8b6e6eddeba2f42910f165681ed64adf7/docs/Security/CVE-2023-23397.md) that the script was specifically looking for strings related to the PidLidReminderFileParameter property within a message and will optionally “clean” it from your Exchange server if found. Upon further research, the PidLidReminderFileParameter is a property that controls what sound file should be played with the Outlook reminder triggered on a user’s device. What Dominic found to be particularly interesting was that a UNC path could be used in that parameter value and trigger an NTLM authentication against a malicious SMB server.
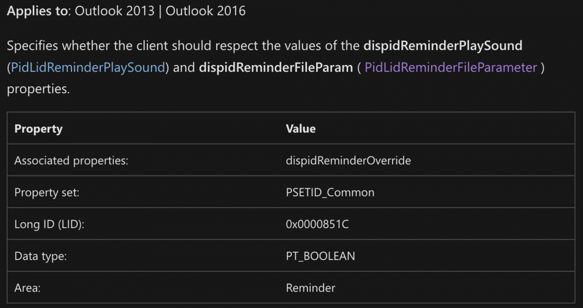
Further analysis of the available Outlook Appointment properties revealed that there was an additional parameter, PidLidReminderOverride, which when flagged true, would trigger the malicious UNC path instead of your usual “ding”.
In the original article, Dominic goes on to explain how to modify the .NET Framework MsgKit library’s Appointment class to create a proof-of-concept. Not long after the release of Dominic’s research other forms of PoC began making their way onto the internet. Of particular interest due to its portability and ease of use was @ka7ana’s PowerShell scripting language PoC which is used in the demonstration video by Assura’s Director of Offensive Security Operations, Nick Berrie (@machevalia).
Assura’s Take
This vulnerability could be a devastating one for organizations. Other security research organizations along with Microsoft have stated the vulnerability can be triggered simply by viewing a malicious invitation in the Outlook preview pane which makes this a “zero-click” privilege escalation vulnerability.
To limit the exploitation of this vulnerability in your organization, we recommend that you prioritize patching your assets with Outlook installed. Beyond patching, to prevent this exploit’s impact and others like it you can take the following precautions:
- Restrict SMB protocol outbound to the Internet. https://support.microsoft.com/en-us/topic/preventing-smb-traffic-from-lateral-connections-and-entering-or-leaving-the-network-c0541db7-2244-0dce-18fd-14a3ddeb282a
- Restrict and protect high-privilege domain and local administrator accounts with Protected Users Group membership.
- Ensure administrative accounts do not have email accounts.
References:
MDSec’s Original Research – https://www.mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/
Microsoft Pass-The-Hash Mitigation Guidance: https://download.microsoft.com/download/7/7/a/77abc5bd-8320-41af-863c-6ecfb10cb4b9/mitigating%20pass-the-hash%20(pth)%20attacks%20and%20other%20credential%20theft%20techniques_english.pdf